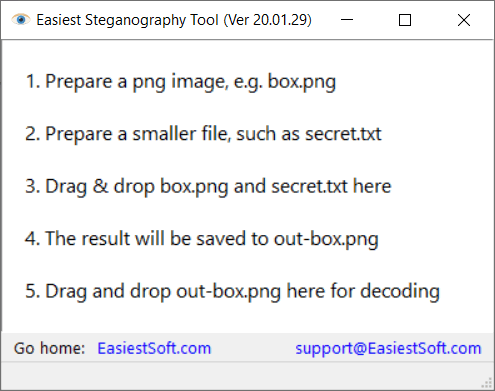
PDF) Image Steganography using Pseudo Random Number Generator | International Journal of Advanced Research in Computer Engineering & Technology (IJARCET) ijarcet - Academia.edu

The secure steganography for hiding images via GAN | EURASIP Journal on Image and Video Processing | Full Text
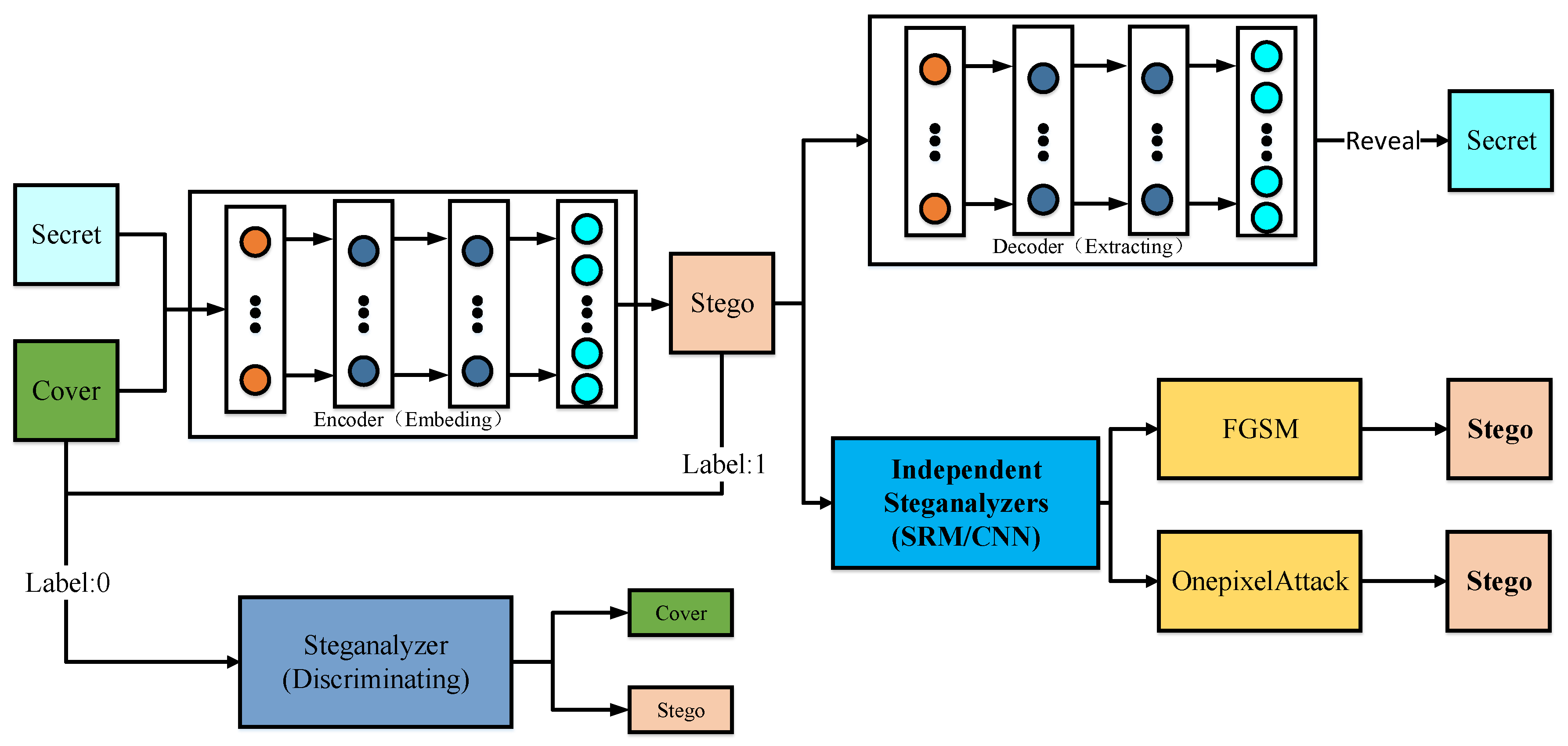
Mathematics | Free Full-Text | Enhancing the Security of Deep Learning Steganography via Adversarial Examples
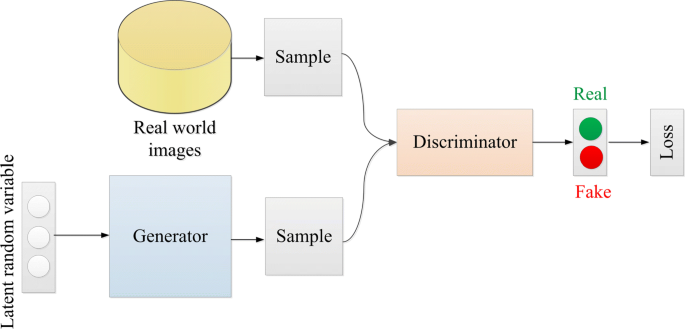
A coverless steganography method based on generative adversarial network | EURASIP Journal on Image and Video Processing | Full Text


![PDF] Steganography using Cryptography and Pseudo Random Numbers | Semantic Scholar PDF] Steganography using Cryptography and Pseudo Random Numbers | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/50032651a42f90ff4156cadbde82d4cccd086cfe/3-Figure2.1-1.png)
![1912.10070] Destruction of Image Steganography using Generative Adversarial Networks 1912.10070] Destruction of Image Steganography using Generative Adversarial Networks](https://ar5iv.labs.arxiv.org/html/1912.10070/assets/images/gan.png)





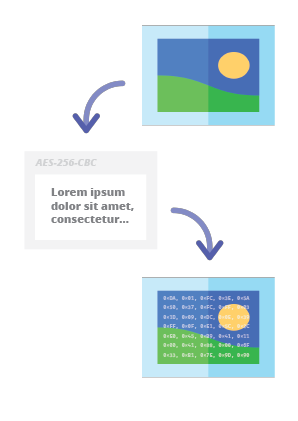
![PDF] QR-DWT Code Image Steganography | Semantic Scholar PDF] QR-DWT Code Image Steganography | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/99adc32297b76f5756aace20635df69fda32f042/3-Figure1-1.png)