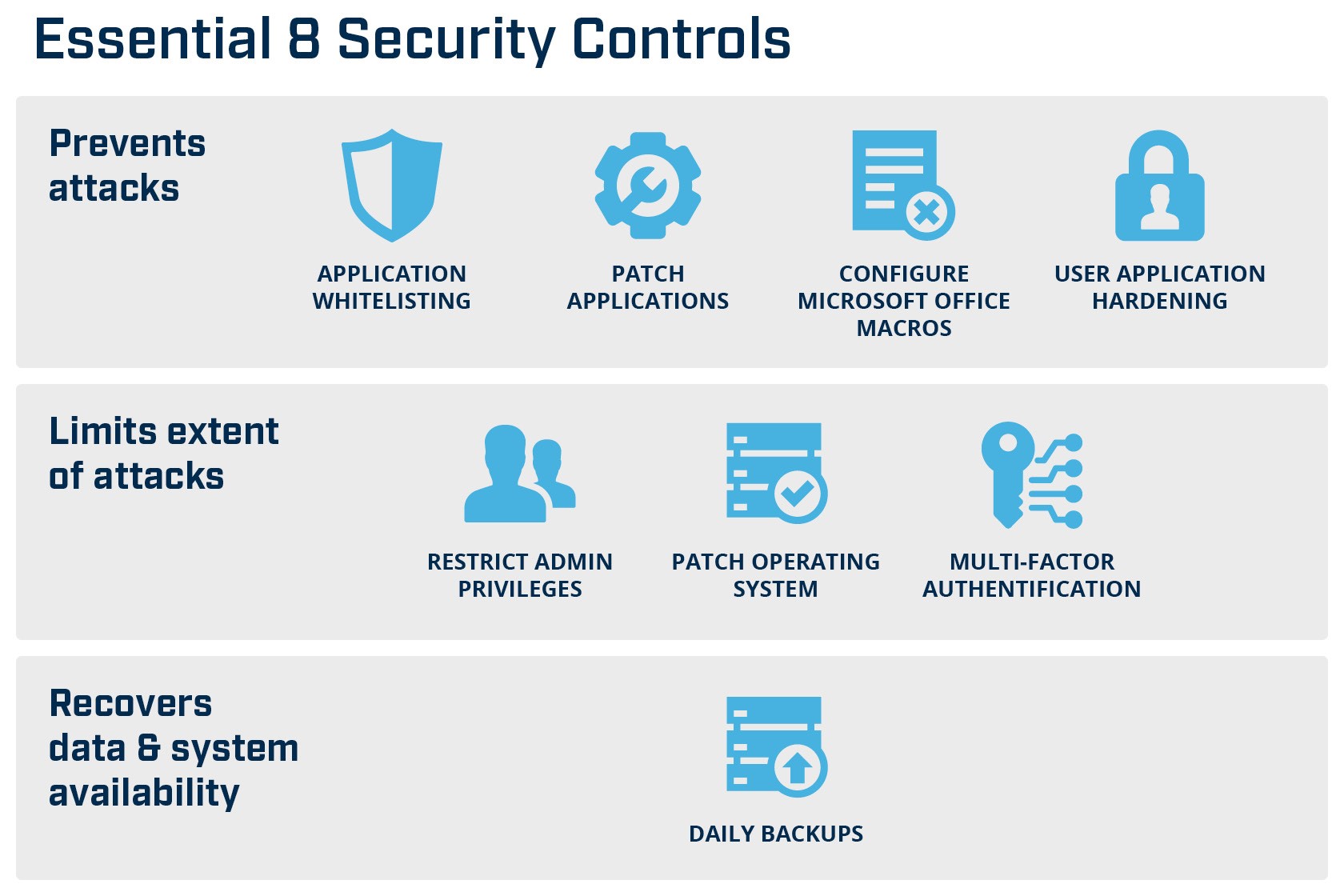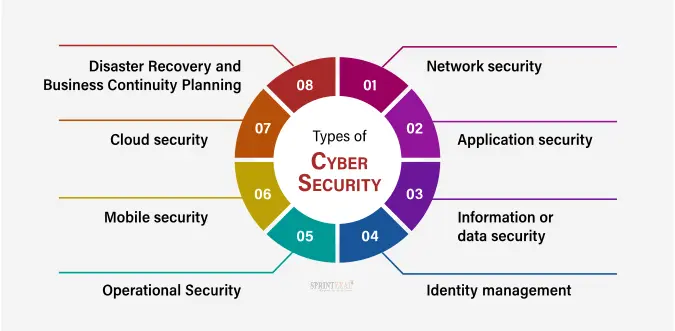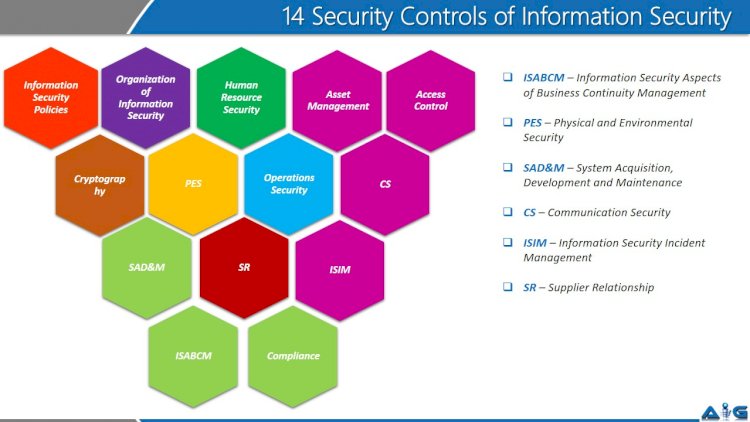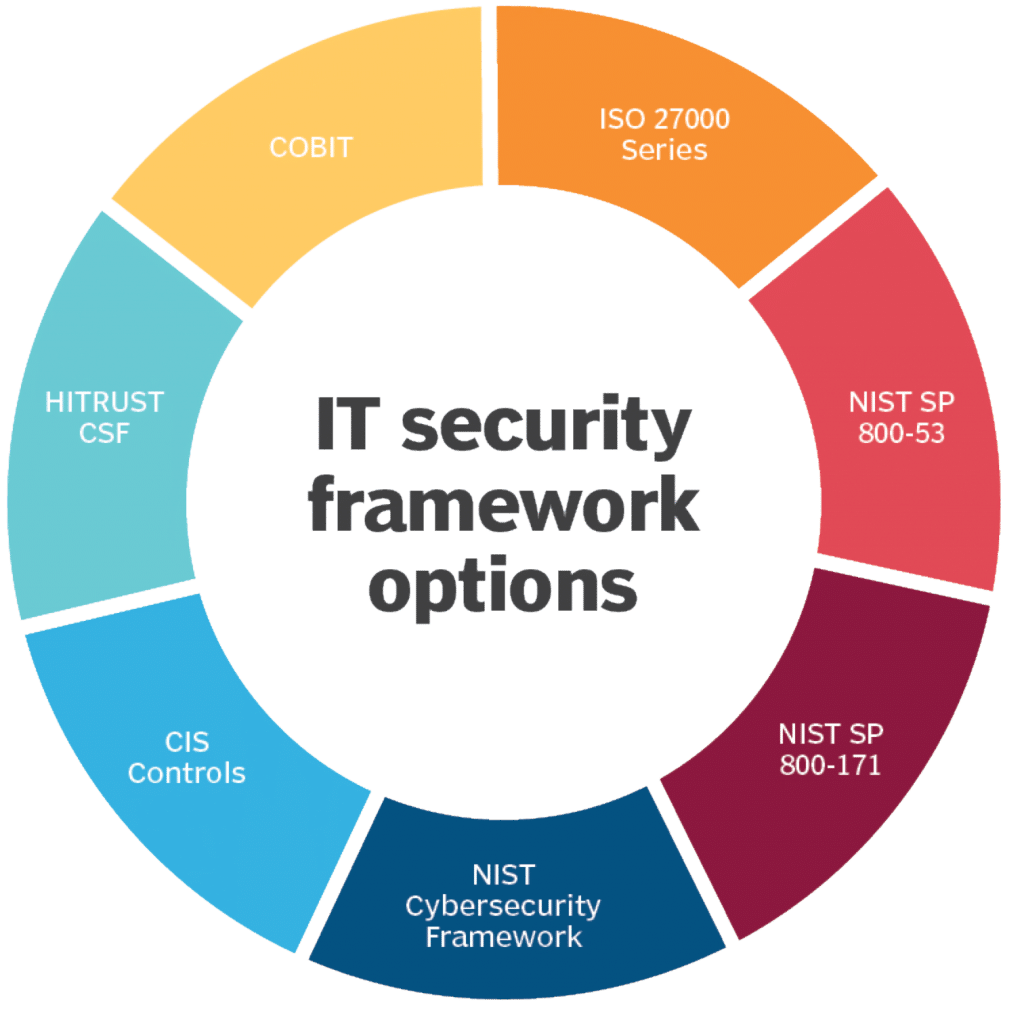
Top 10 IT security actions: No. 3 managing and controlling administrative privileges - ITSM.10.094 - Canadian Centre for Cyber Security

Compensating Controls vs Defense-in-depth Strategy by Wentz Wu, ISSAP, ISSEP, ISSMP CISSP, CCSP, CSSLP, CGRC, SSCP, CC, CISM, CISA, CRISC, CGEIT, PMP, ACP, PBA, RMP, CEH, ECSAWentz Wu