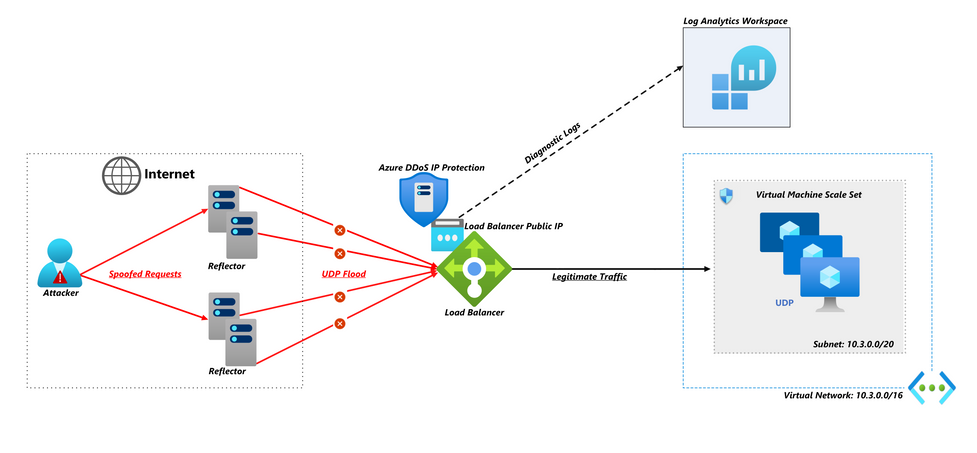
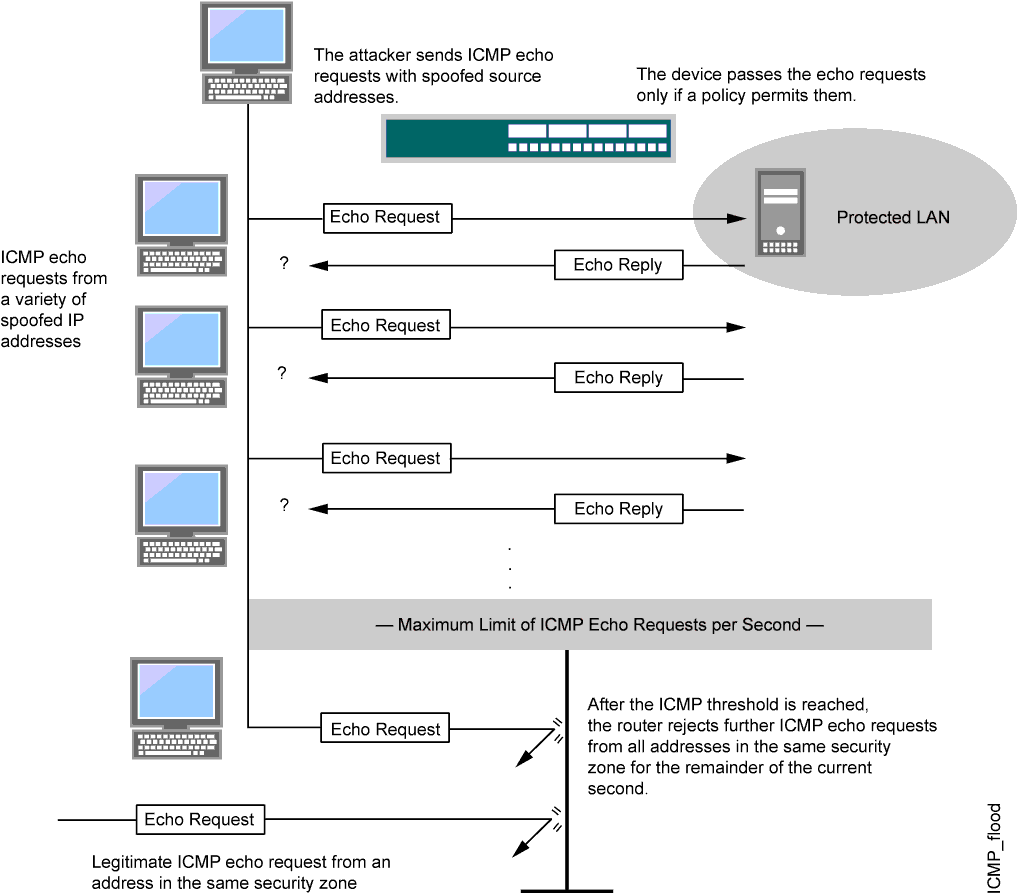
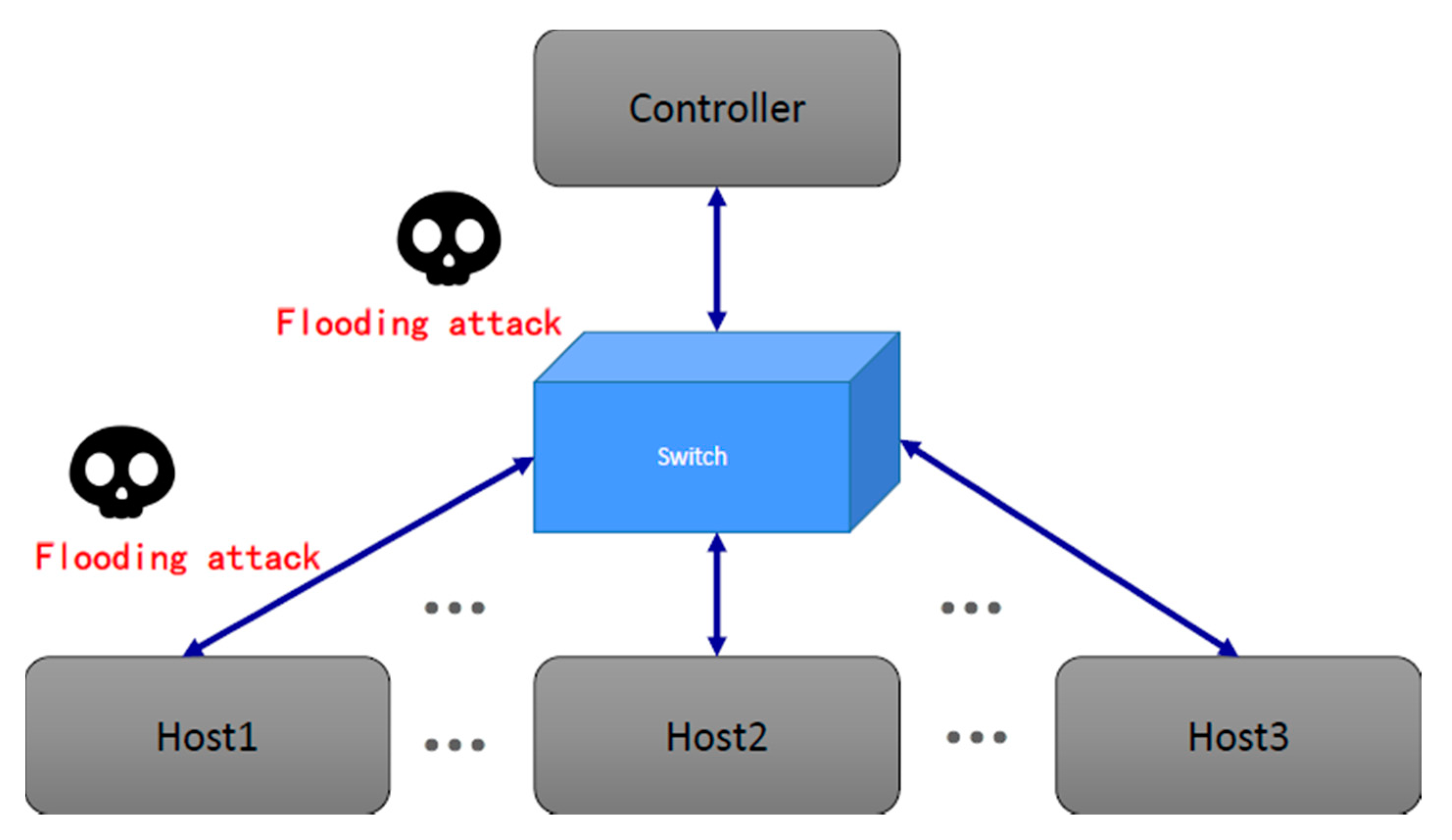
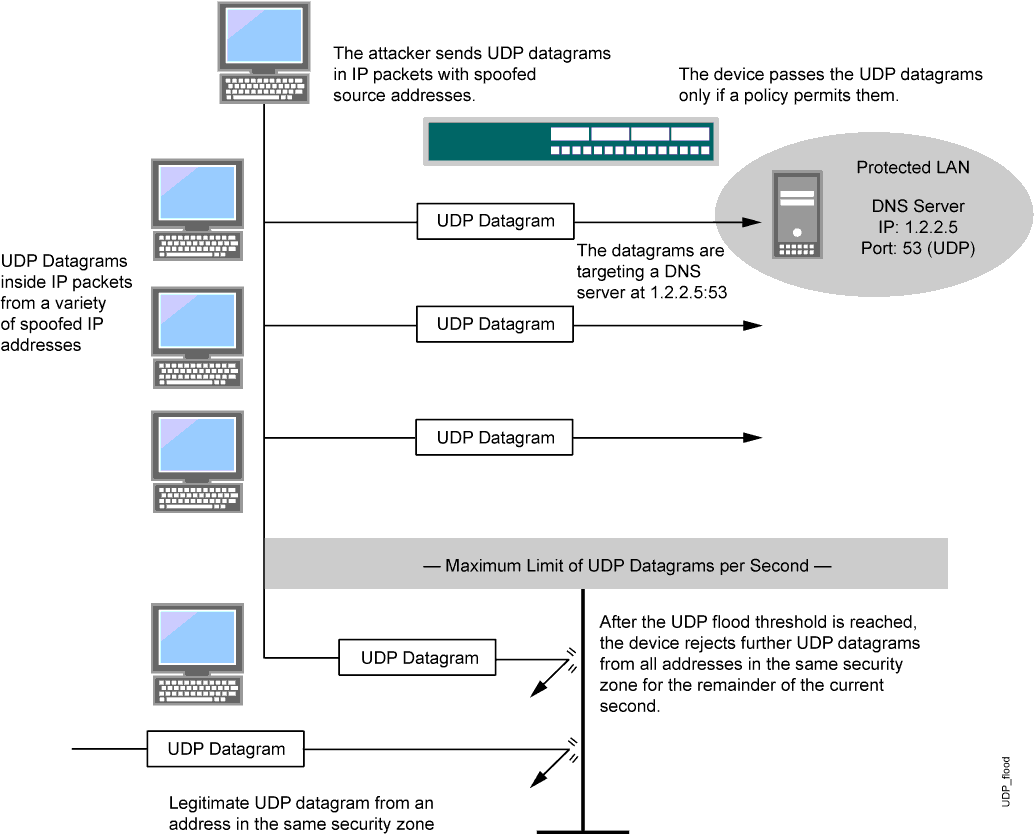
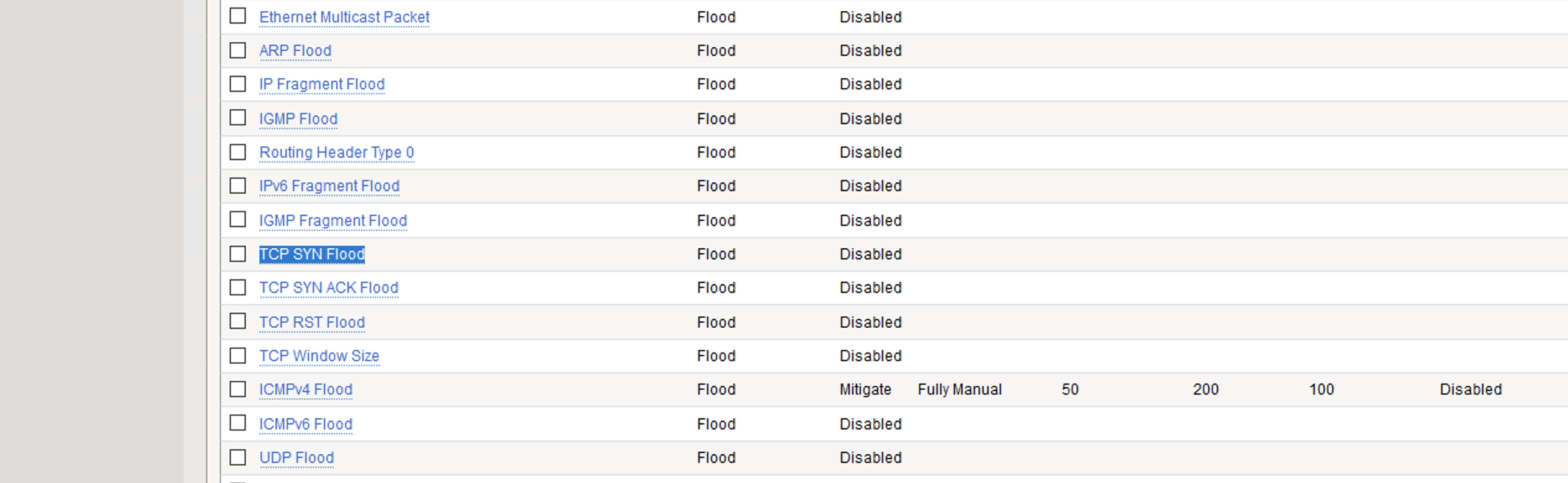
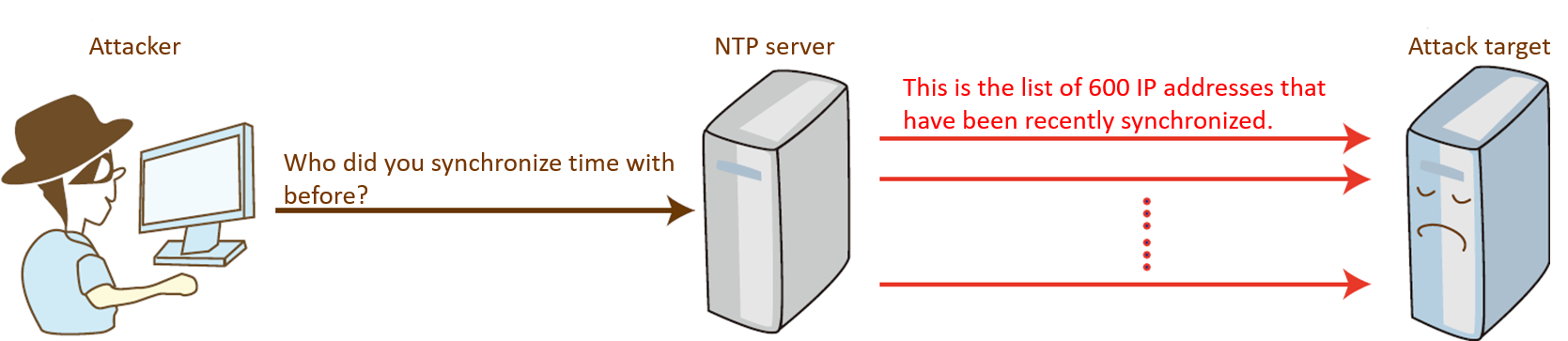
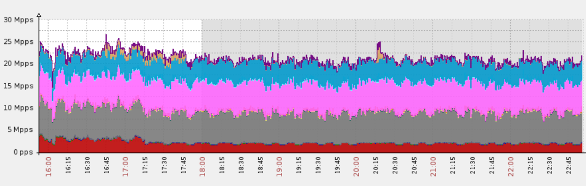
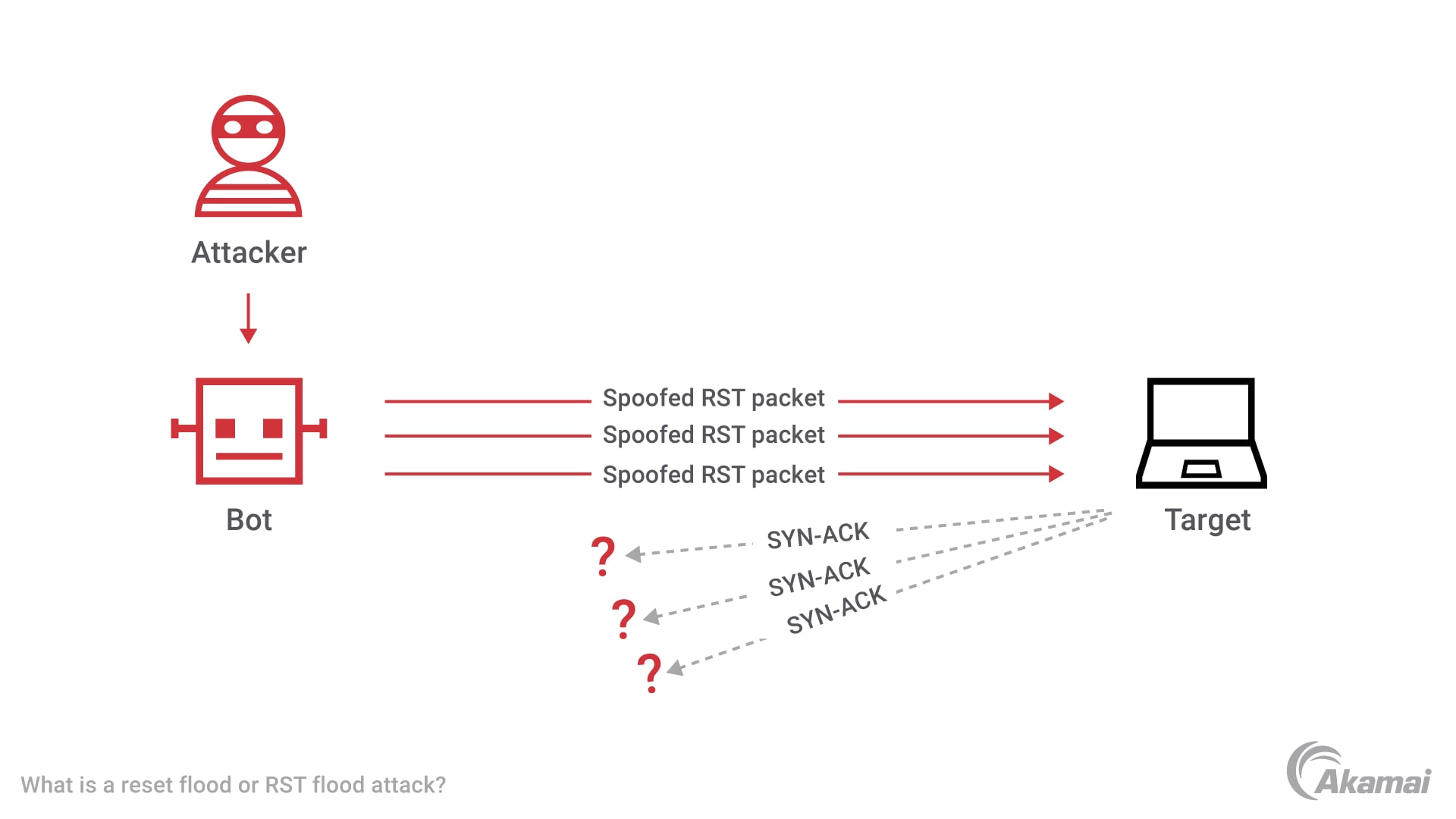
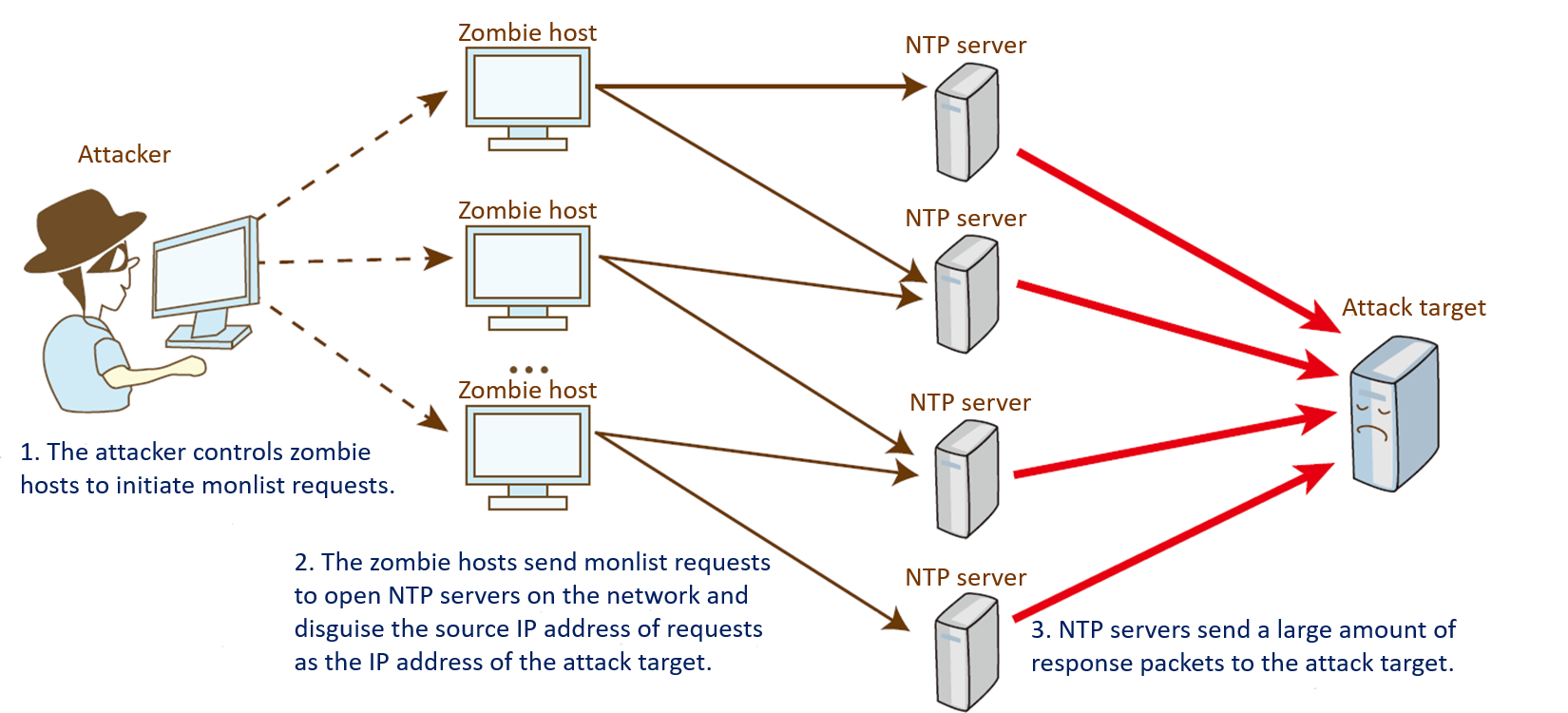
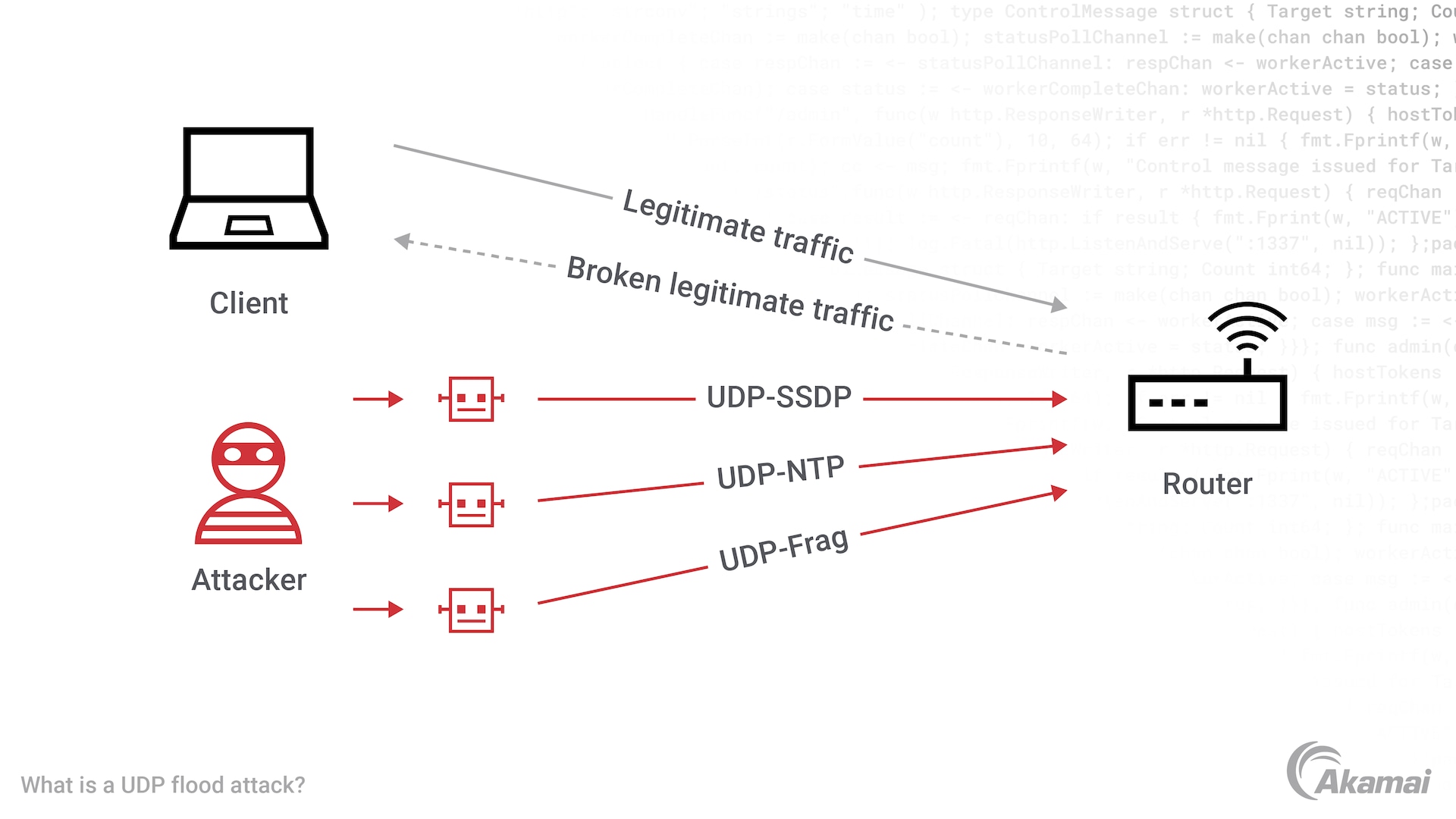
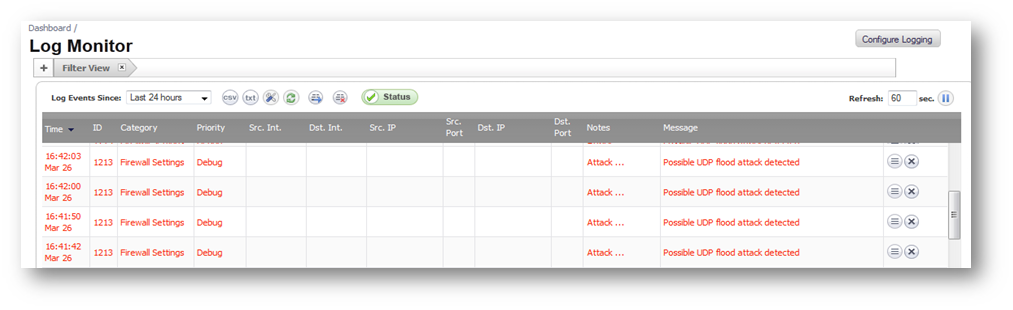
plz help : i have Detected stationary source udp flood attack in my TL-ER5120 loadbalancer - Business Community

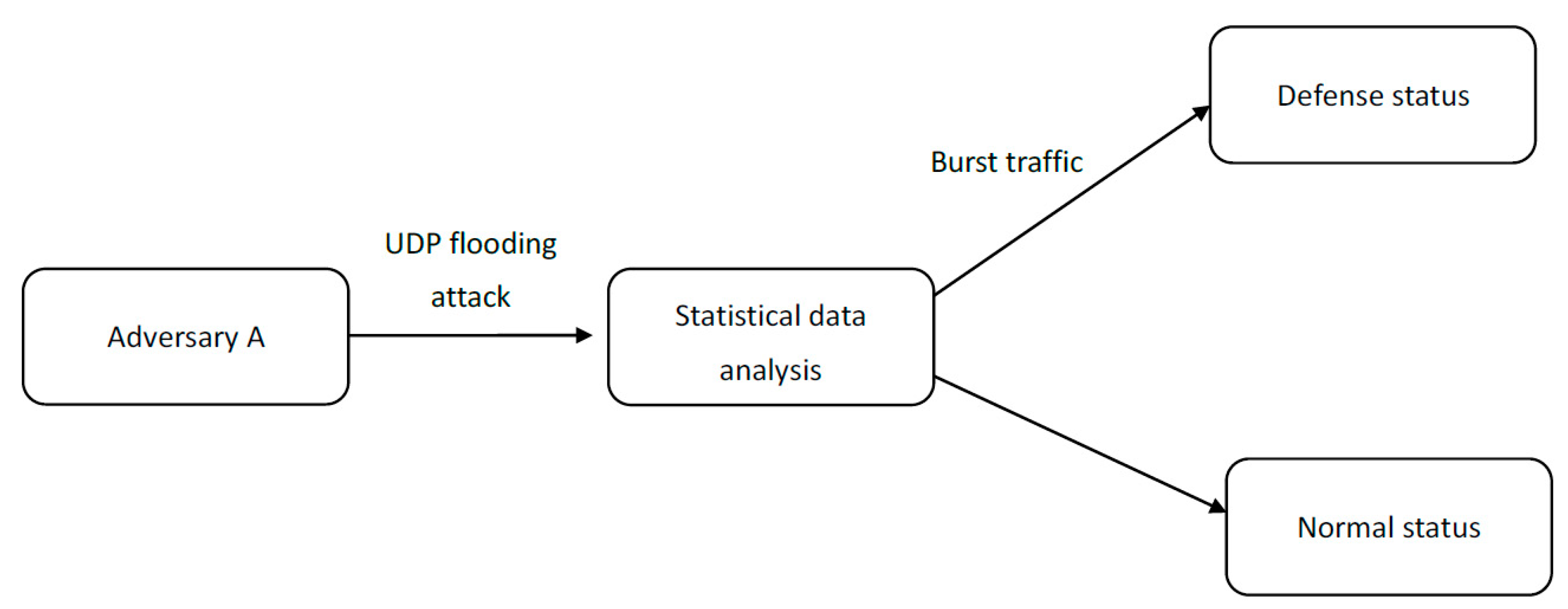
First layer of SOM for classifying UDP flood attack using ICMP flood... | Download Scientific Diagram

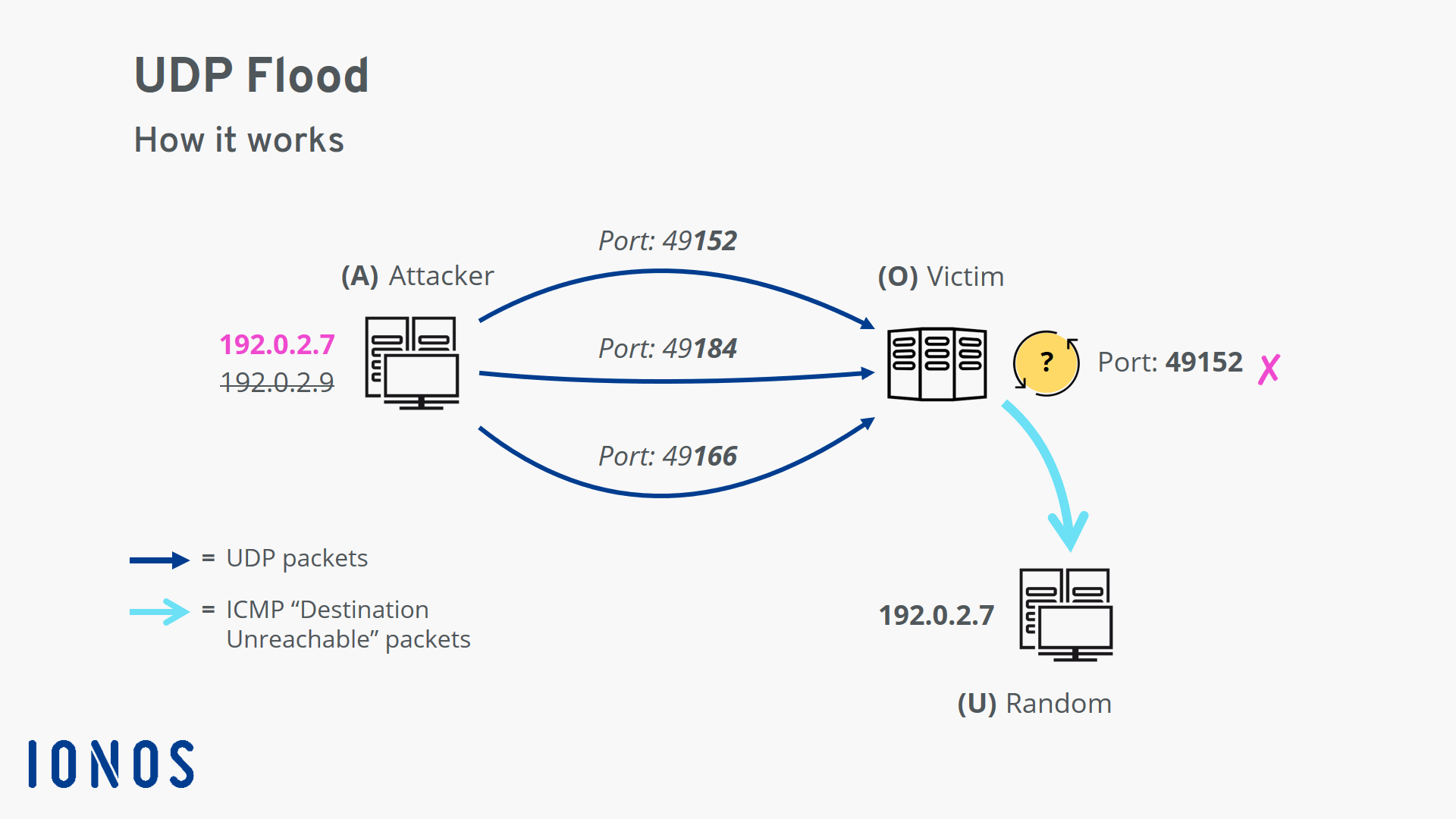
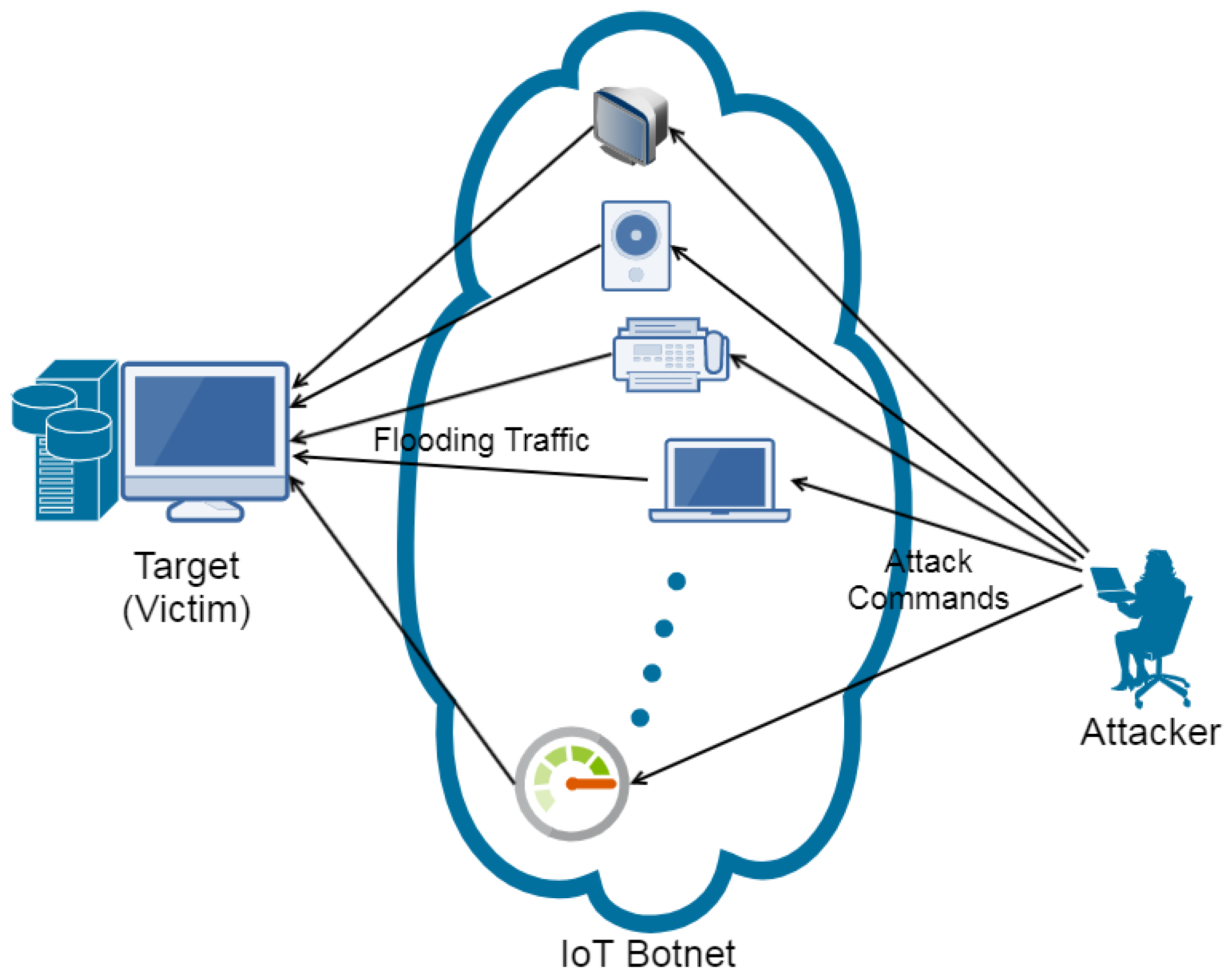
Basic UDP Flood Attack. DDOS and Anti-DDOS methods. Articole introductive si ajutor | Evidweb Network