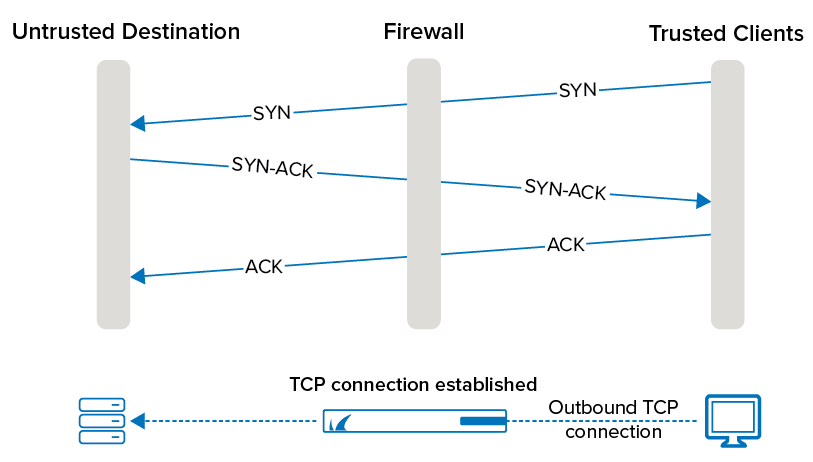
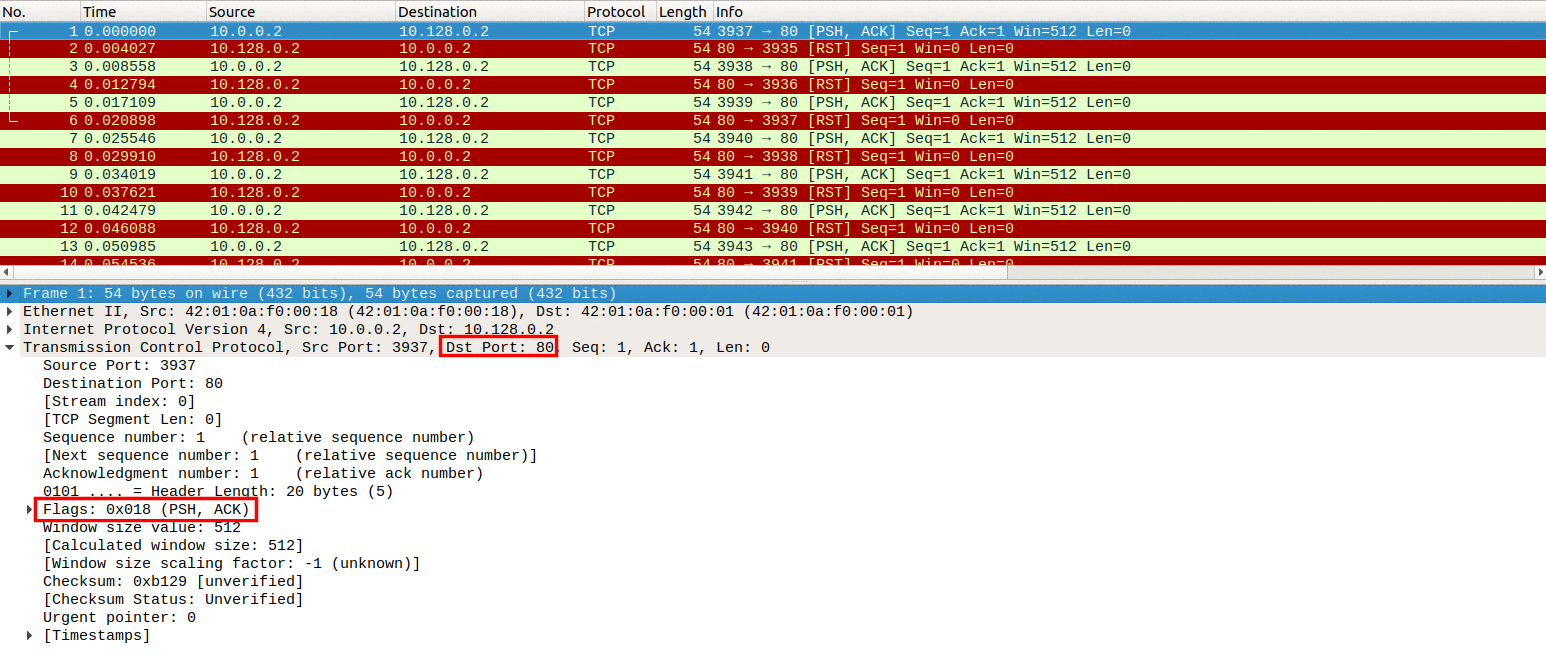
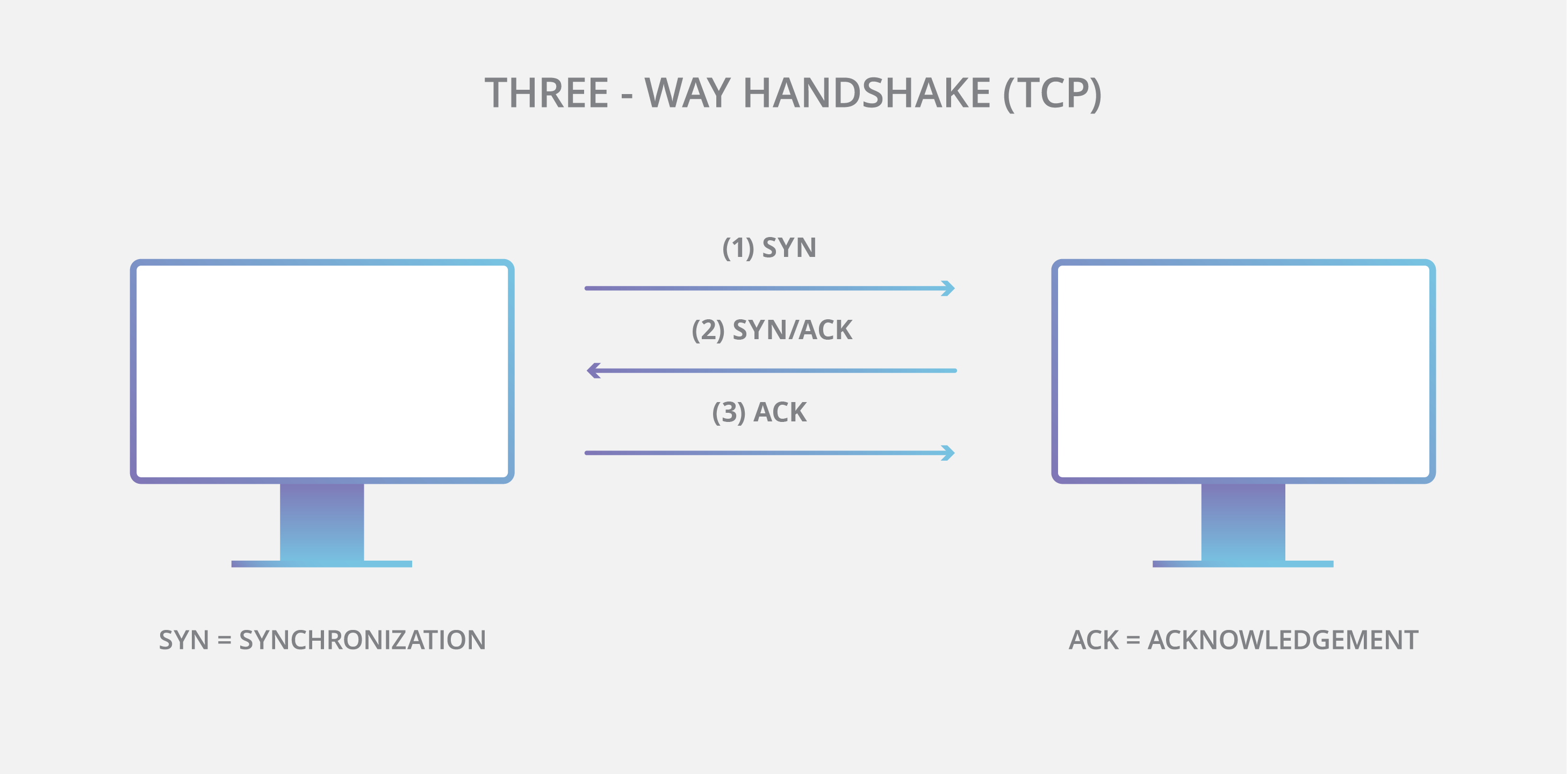
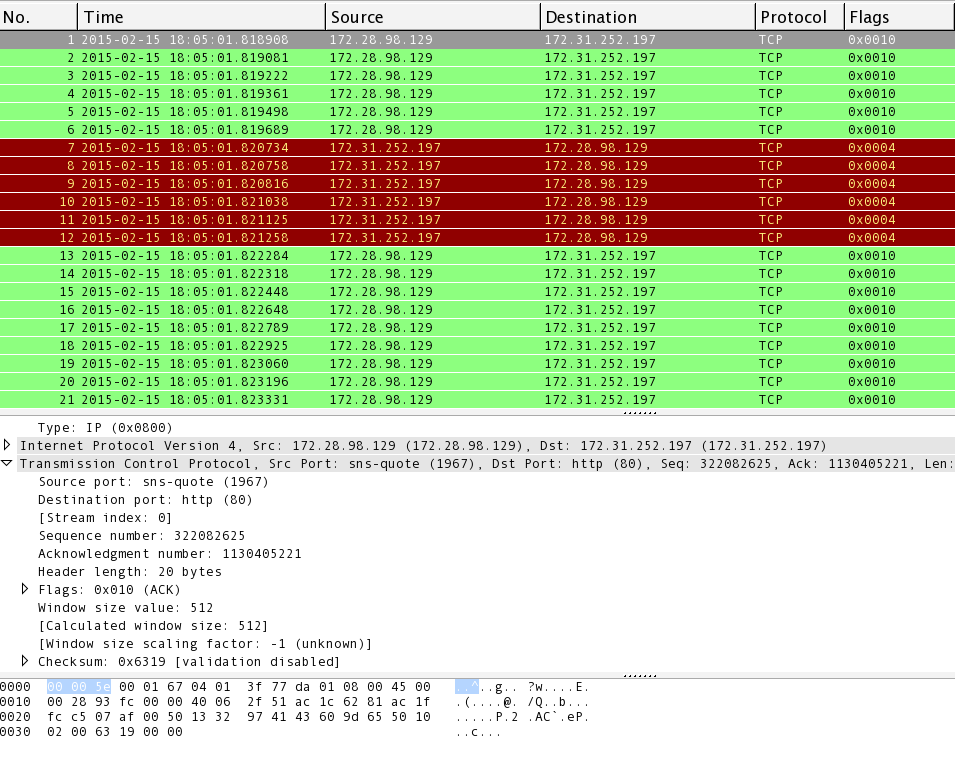
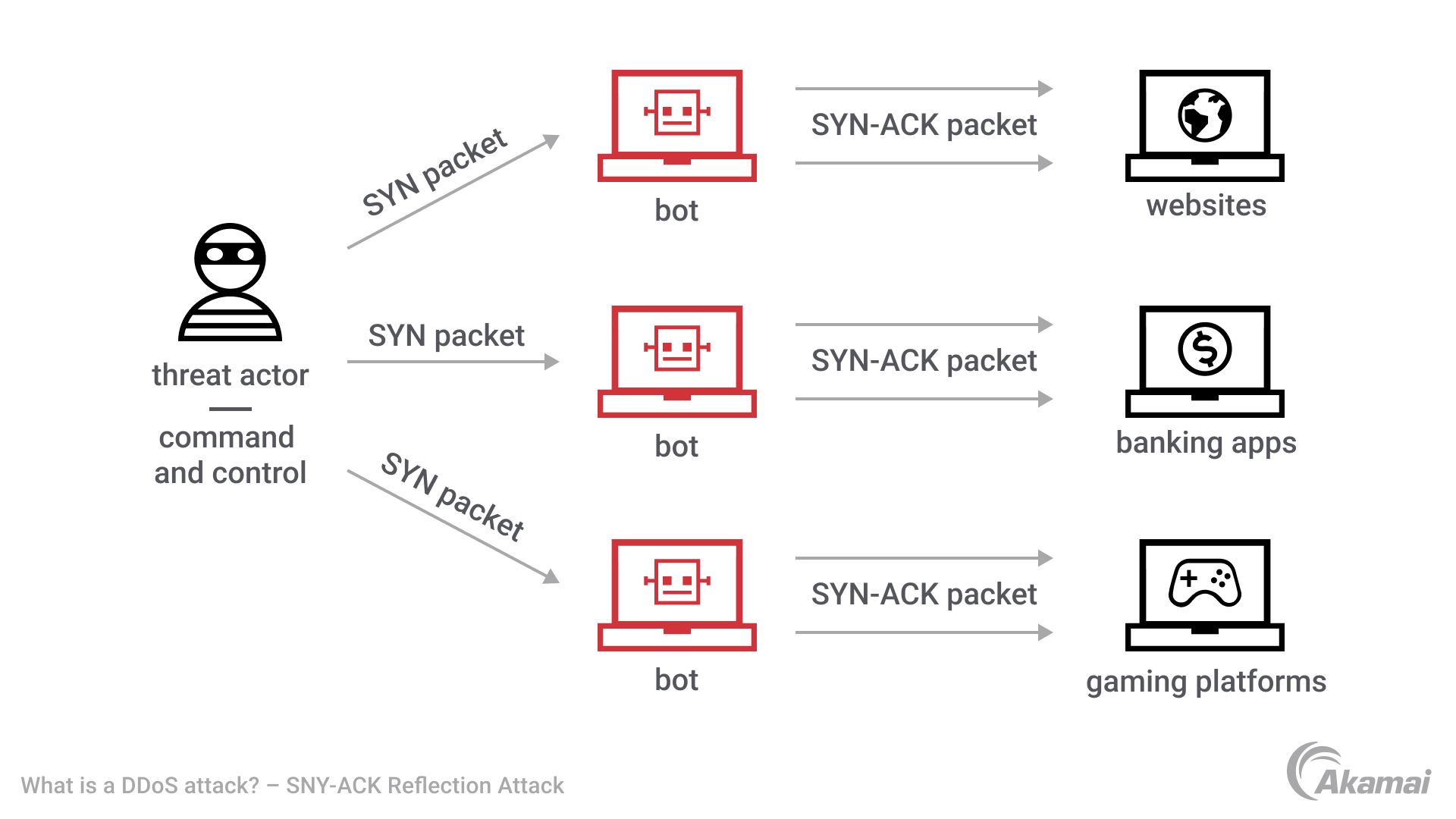
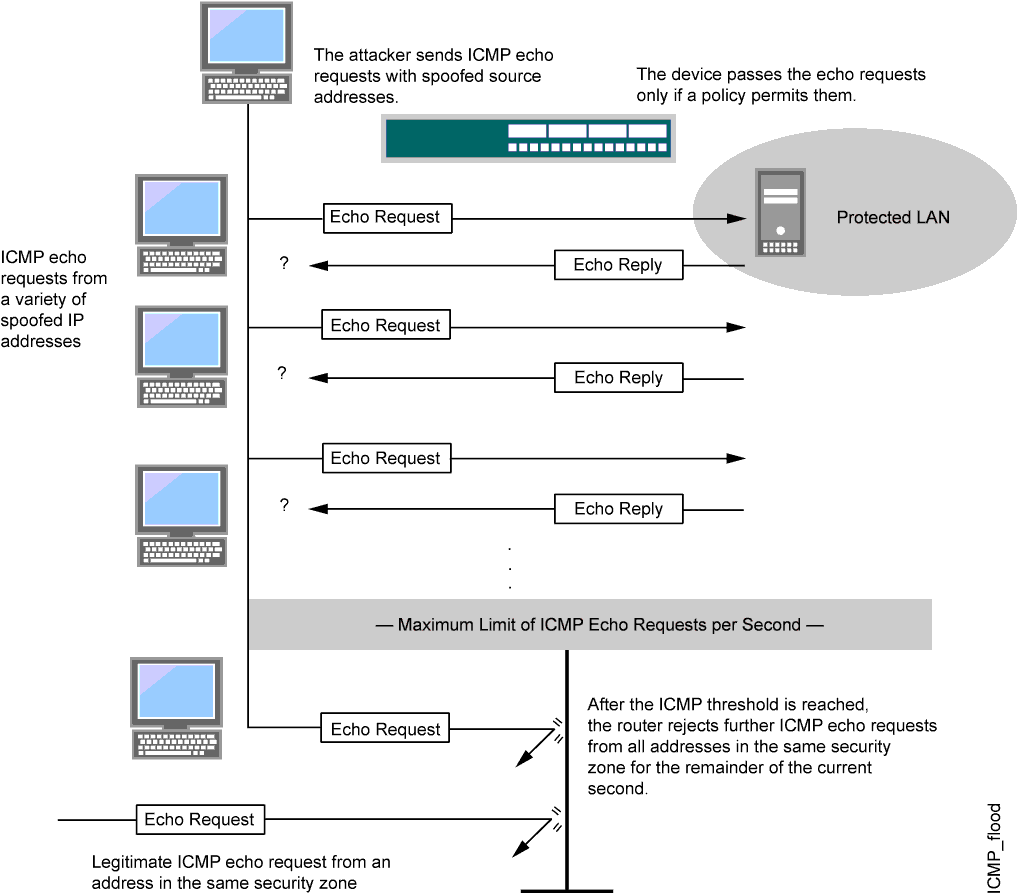
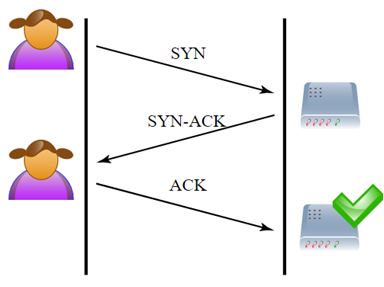
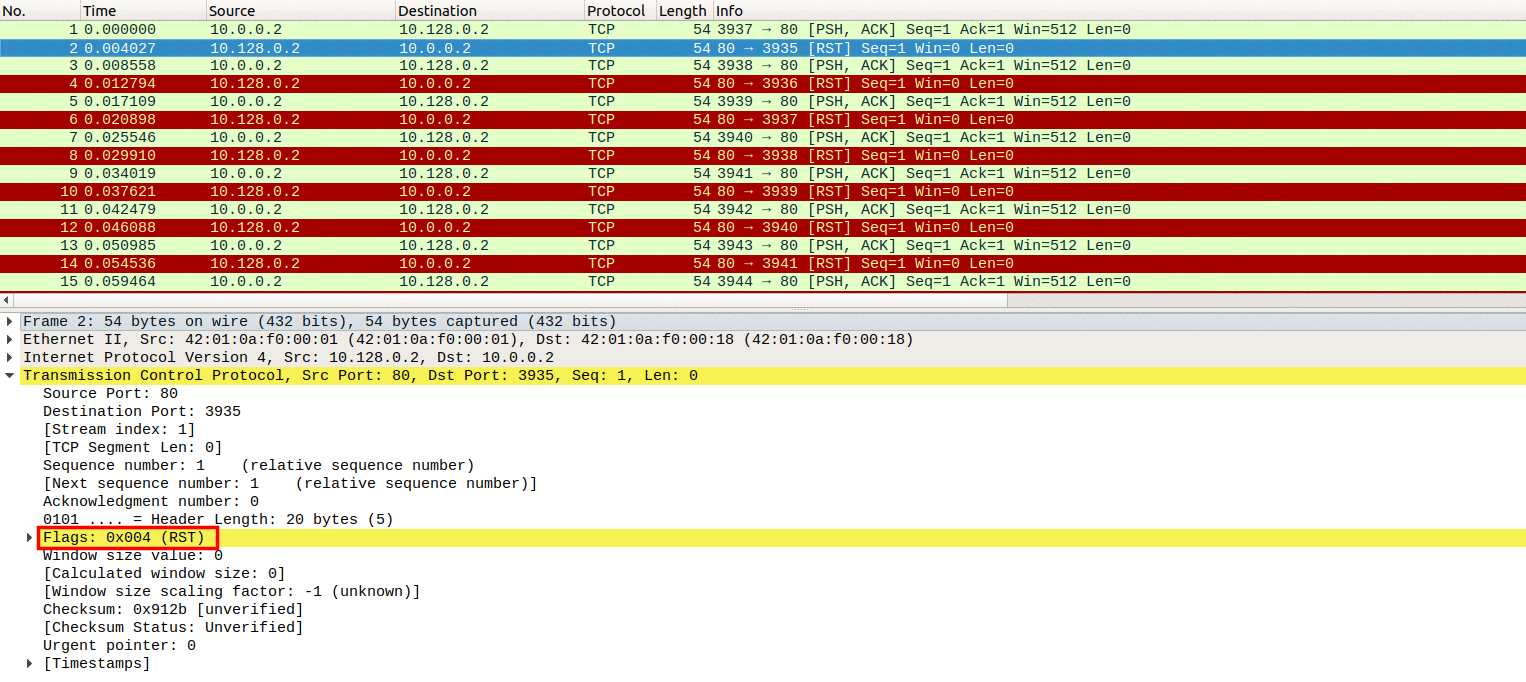
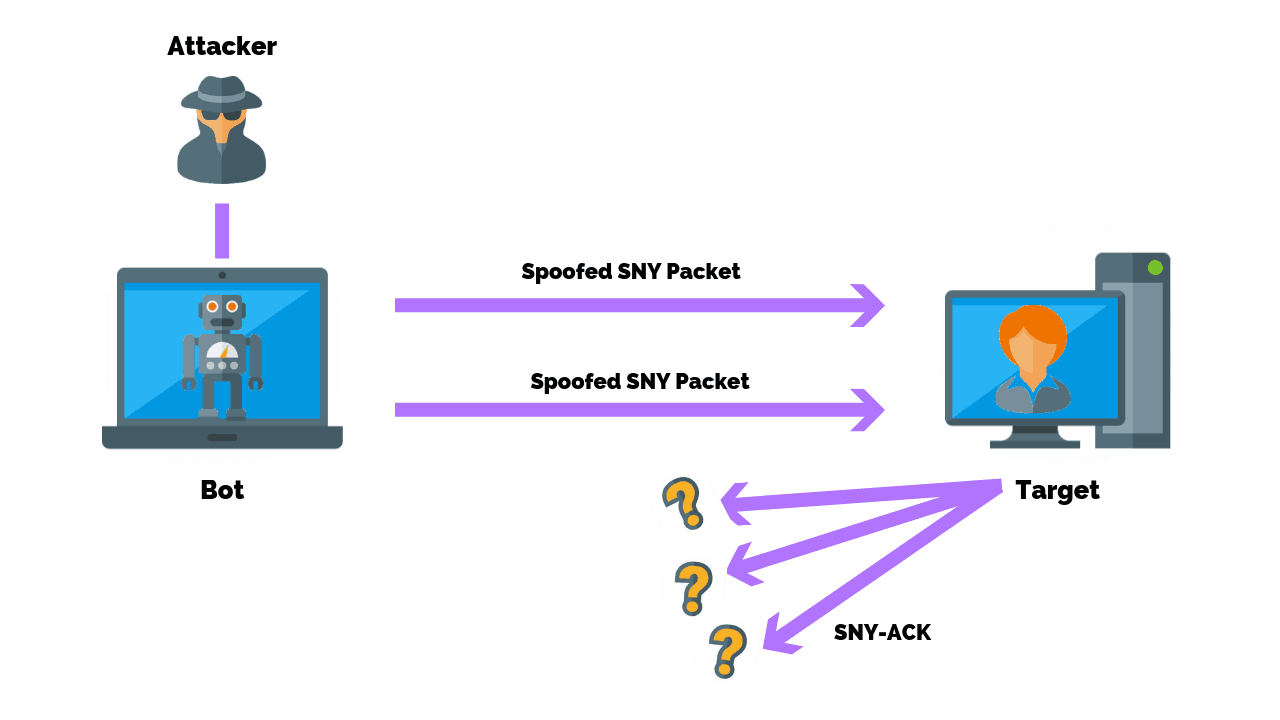
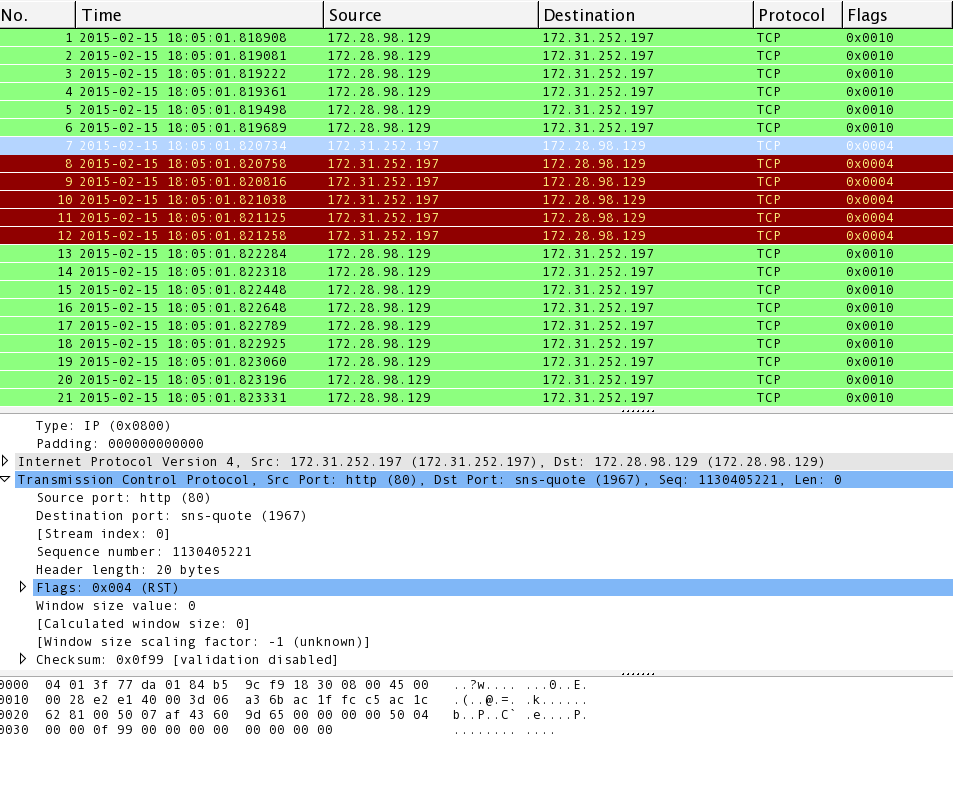
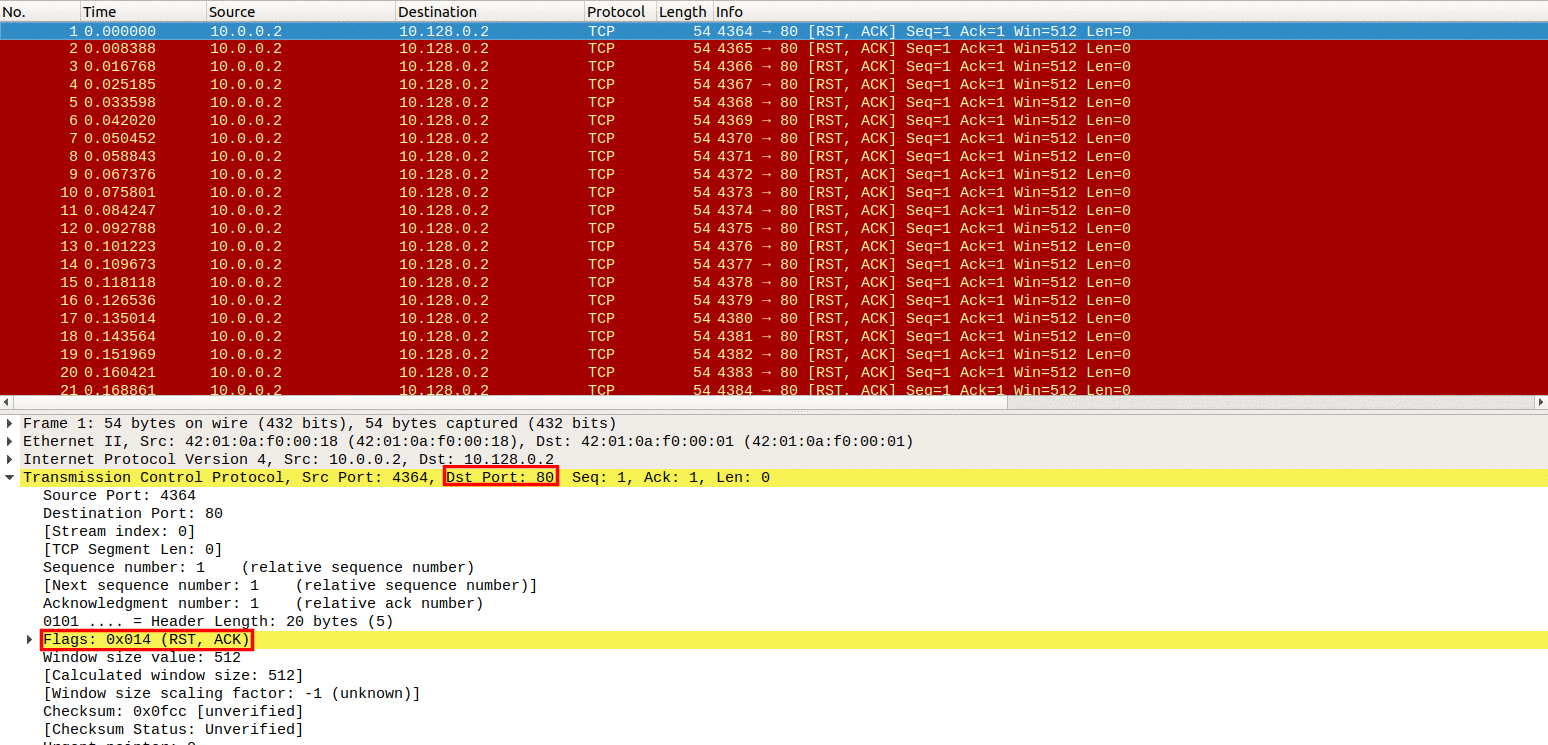
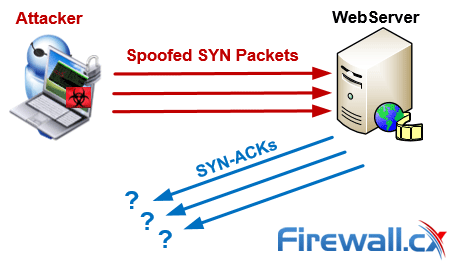
SYN-ACK-ACK proxy flood process. To initiate this attack on Juniper... | Download Scientific Diagram

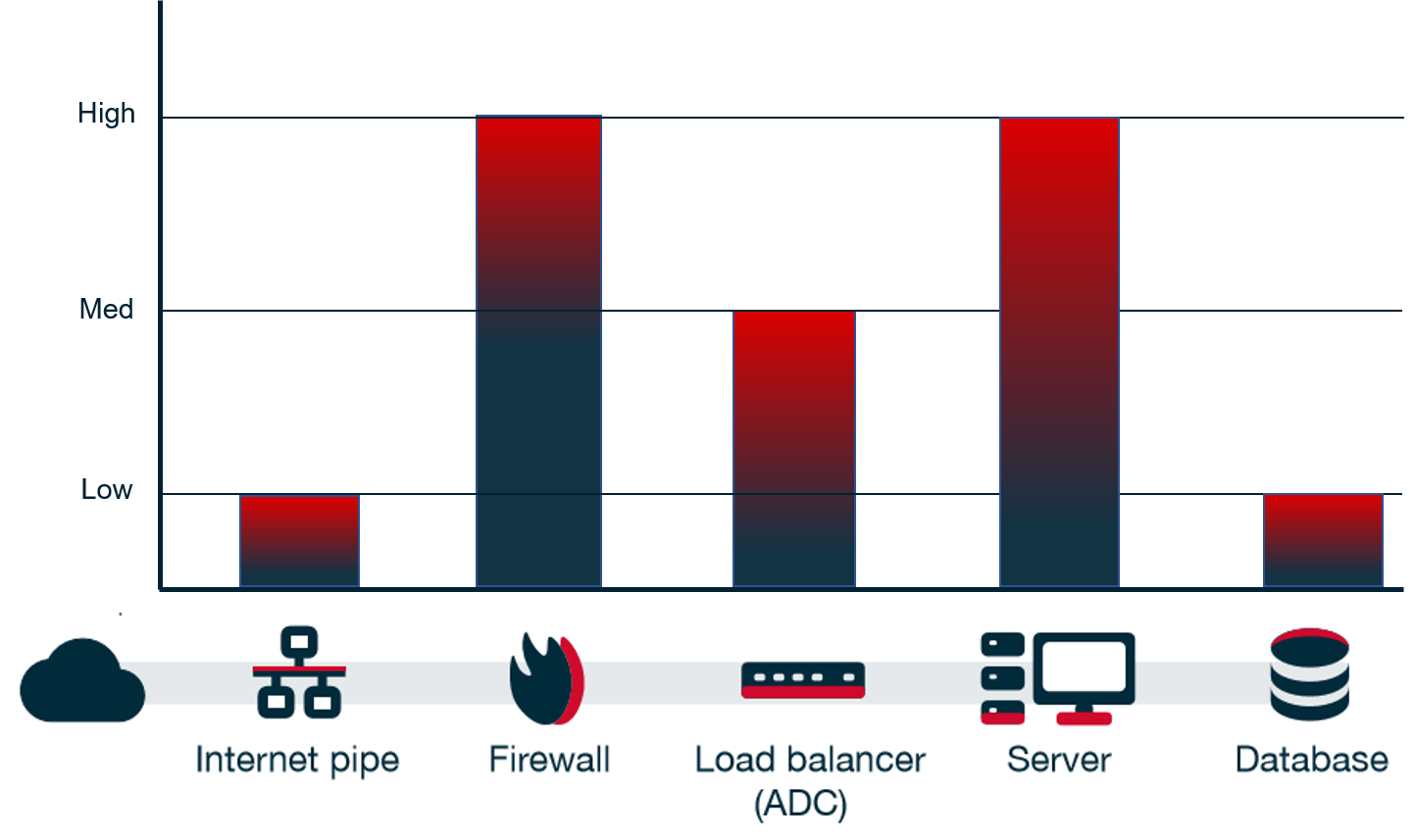
a) shows the results of the C-RAD TCP SYN/ACK flood test. C-RAD defeats... | Download Scientific Diagram

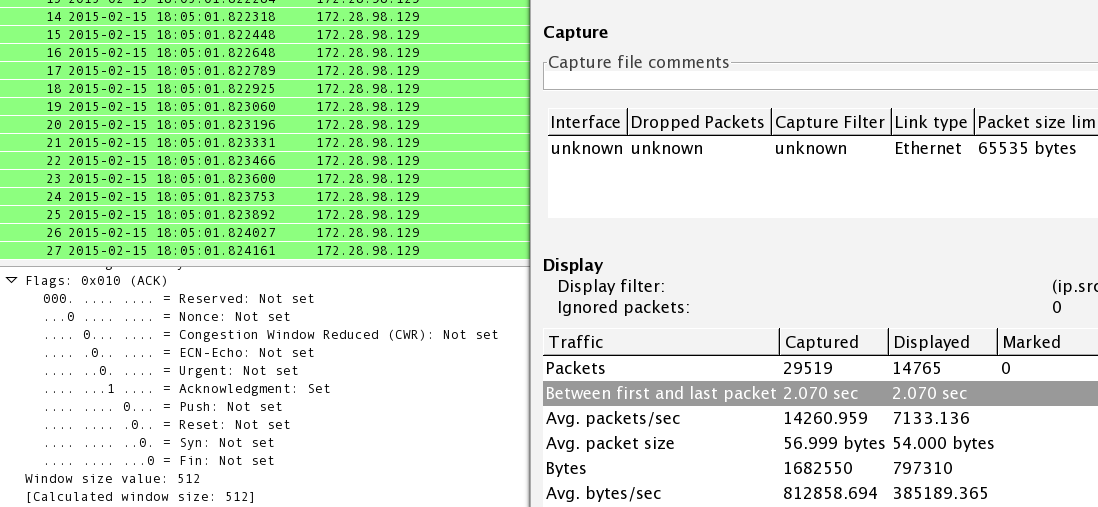
Exemplifying test on a single trace (Darpa 1 with StachelDraht TCP ACK... | Download Scientific Diagram