
Attribute based access control in Pega (ABAC) | Pega Help | Case Management | Integration | Data Pages

Configuring Geolocation Access Control Rules to Block or Allow Requests from Specific Locations_Web Application Firewall_User Guide_Policies
![Cisco Secure Firewall Management Center Device Configuration Guide, 7.2 - Access Control Rules [Cisco Secure Firewall Management Center] - Cisco Cisco Secure Firewall Management Center Device Configuration Guide, 7.2 - Access Control Rules [Cisco Secure Firewall Management Center] - Cisco](https://www.cisco.com/c/dam/en/us/td/i/400001-500000/450001-460000/454001-455000/454592.jpg)
Cisco Secure Firewall Management Center Device Configuration Guide, 7.2 - Access Control Rules [Cisco Secure Firewall Management Center] - Cisco
![Firepower Management Center Configuration Guide, Version 6.2 - Access Control Policies [Cisco Secure Firewall Management Center] - Cisco Firepower Management Center Configuration Guide, Version 6.2 - Access Control Policies [Cisco Secure Firewall Management Center] - Cisco](https://www.cisco.com/c/dam/en/us/td/i/400001-500000/400001-410000/405001-406000/405096.jpg)
Firepower Management Center Configuration Guide, Version 6.2 - Access Control Policies [Cisco Secure Firewall Management Center] - Cisco

Which subset of access control rules on DB can ensure confidentiality... | Download Scientific Diagram





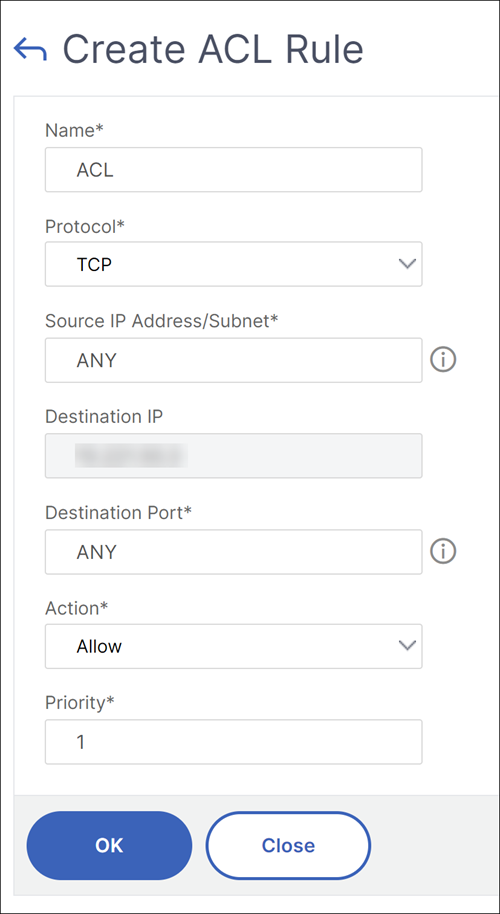

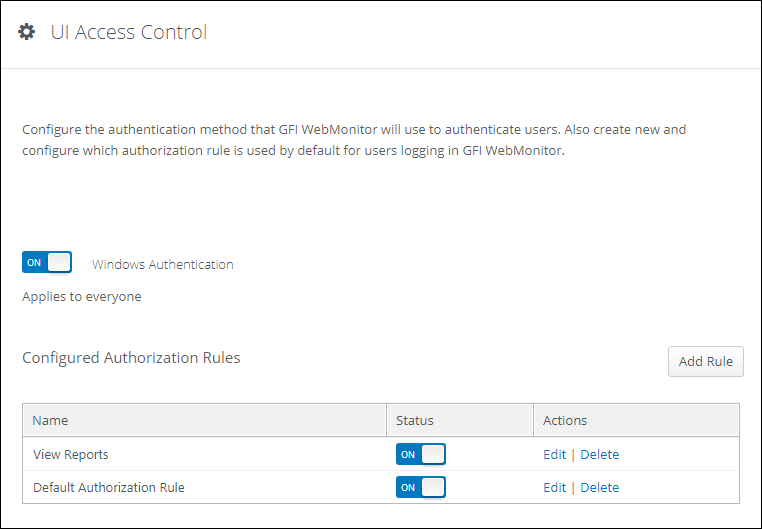

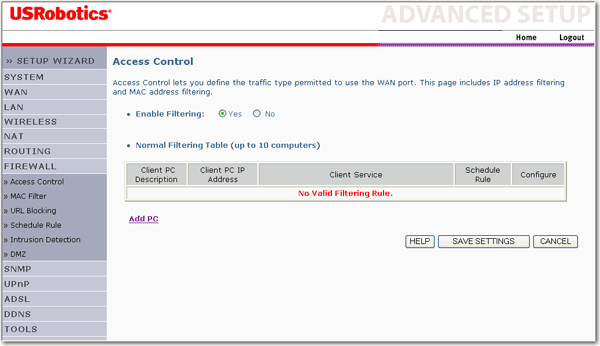
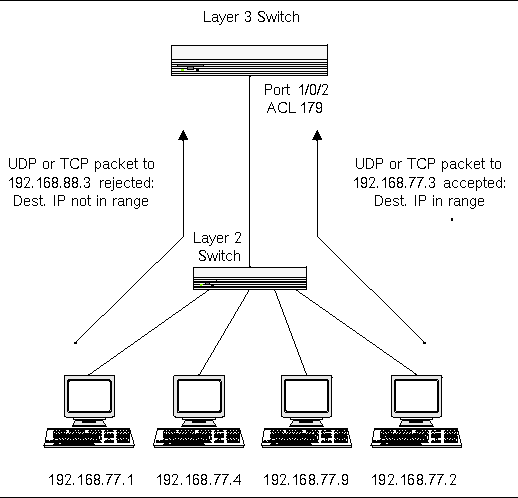

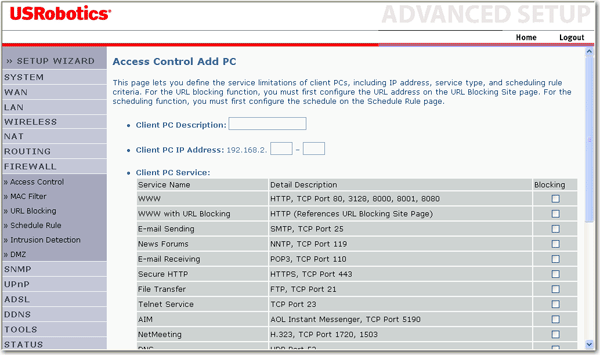
![Defining access control [PRO] Defining access control [PRO]](https://gatographql.com/assets/guides/upstream-pro/access-control-list.png)
